Securing APIs is now an imperative for every organisation. They are the arteries of the modern digital world, generating almost 71 % of the world's Internet traffic. However, each of their connections can become a gateway for malicious attacks. cyber attacks. Protecting your APIs means not only preserving the confidentiality of your data, but also ensuring the reliability and durability of your digital infrastructure. Discover the tried and tested methods for combating attacks and data leaks.

The API are at the heart of contemporary software architecture, acting as indispensable connectors. They enable different applications to communicate with each other, exchange data seamlessly and drive third-party services, creating complex, interdependent digital ecosystems.
So much so that recent studies show that APIs generate most of the world's Internet traffic.
71 % of the world's Internet traffic comes from API-based exchanges
Imperva/Thales report, 2024
However, this increased interconnection, while beneficial for innovation and development, simultaneously creates a considerable number of attack surfaces for the cybercriminals.
A Poorly protected API or inadequately secured can have serious and costly consequences, including :
- L'exfiltration of sensitive dataincluding confidential personal, financial or medical information, which can be sold on the black market or used for fraud.
- From denial of service (DoS/DDoS)where the API is overwhelmed by a massive volume of malicious requests, rendering services inaccessible to legitimate users.
- From identity theft and escalations of privilegesallowing attackers to access systems with greater rights than those initially assigned to them.
- A reputational damage of the company, which can lead to a loss of confidence among customers, as well as financial losses costs. remediationregulatory fines and loss of sales.
Securing APIs is therefore not just a technical 'bonus' to be taken lightly, but a strategic imperative.
It must be based on a multi-layered approach, covering authentication, authorisation, flow protection, code robustness and continuous monitoring.
However, according to a Cloudflare study published in 2024, up to 25 % of endpoints APIs are not documented. These APIs, often referred to as shadow API These "ghost APIs" escape the supervision of security teams, considerably increasing the risk of vulnerabilities.
What's more, the rise of AI, and more specifically of LLM such as ChatGPT has led to a dramatic increase in the use of bots.
Why secure APIs? New threats
The massive adoption of microservices-based architectures has triggered an explosion in the creation of APIs.
In a microservices architecture, each individual service generally requires its own interface, which leads to the creation of a complex network of APIs. This network can become extremely difficult to control centrally.
This proliferation has direct and far-reaching consequences for security, as many companies are seriously struggling to maintain a complete and accurate inventory of all their APIs in production.
The shadow API scourge
The " Shadow API" or shadow APIs, are API access points that are often introduced by developers or individual users for specific functions, without being properly documented or subject to security and safety processes. governance of the organisation. They represent a significant attack surface that is not monitored by the Information Systems Department (ISD).
For example, Cloudflare discovered almost 31 % additional REST APIs than those identified by the session identifiers provided by their customers, underlining the scale of this problem.
The explosion of bad bots
The explosion in malicious bot traffic is a major catalyst for API security incidents.
While some of this traffic is generated by legitimate bots (for web indexing, for example), an alarming proportion is generated by malicious bots.
For the first time, in 2024, traffic generated by bots has surpassed that generated by humansreaching 51 % of all web traffic. A significant proportion of this traffic is automated, 37 %, was generated by malicious botsThese are 'bad bots', according to Imperva's Bad Bot Report 2025.
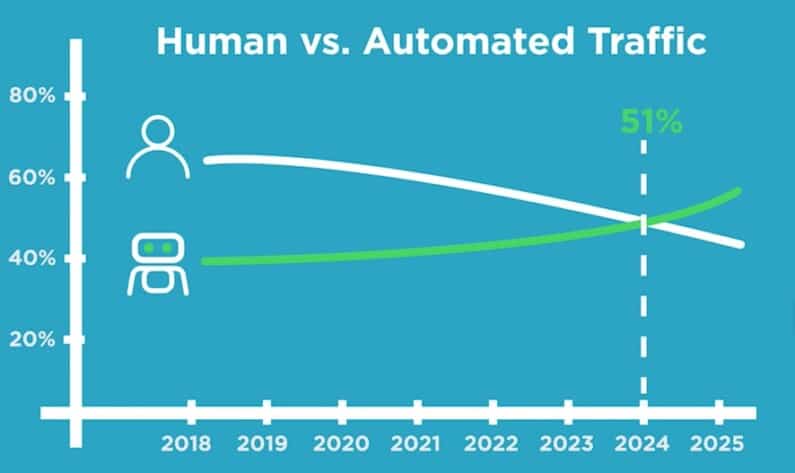
The increased accessibility ofGenerative AI has considerably lowered the barrier to entry for cybercriminals, enabling them to create and deploy malicious bots on a massive scale.
In 2024, Imperva blocked an average of 2 million AI-powered cyber attacks every day. Attackers are using AI not only to generate bots, but also to refine their techniques to evade detection more effectively.
APIs, targets of bad bots
APIs have become a prime target for these sophisticated bots. In 2024, 44 % of advanced bot traffic targeted APIs, compared with just 10% for traditional web applications. Bots are no longer content to overwhelm API endpoints; they are exploiting the business logic underlying these systems to commit fraud, extract data and bypass security controls. For example,25 %% attacks mitigated by Imperva specifically targeted and abused API business logic.
The economic consequences are alarming. Insecure APIs, combined with automated bot attacks, potentially generate $186 billion in annual losses for businesses.
The average company manages up to 613 API endpointsaccording to a 2024 Imperva Threat Research study. Large companies, particularly those with sales in excess of €1 billion, are two to three times more likely to suffer API-related security incidents.
The main risks of not securing APIs
APIs are vulnerable to a multitude of attacks, often identified by theOWASP (Open Web Application Security Project). Here are the most common threats and their implications:
- Broken Object-Level Authorization (BOLA)
This is the vulnerability the most critical according to OWASP. It allows unauthorised users to access resources that are not intended for them.
For example, an API may correctly authenticate a user, but accept a different identifier in the request parameter, allowing access to another user's account details.
The Authy (Twilio) incident in July 2024, where malicious actors exploited an insecure API endpoint to access 33 million phone numbers, is a striking example.
- Broken User Authentication
These authentication vulnerabilities allow unauthorised users to access the API by exploiting weak or compromised authentication methods. This can include man-in-the-middle "These attacks are designed to steal valid session tokens. Incorrect implementation of authentication mechanisms can allow attackers to compromise authentication tokens or exploit vulnerabilities to temporarily or permanently impersonate other users.
- Excessive Data Exposure
Developers often inadvertently expose more data than necessary via their APIs, returning sensitive or confidential information that is not explicitly requested by the end user. This excess data can be intercepted and exploited.
- Lack of Resource and Rate Limiting
The absence of strict controls on the number of requests a client can make to an API in a given time period makes APIs extremely vulnerable to attacks by denial of service (DoS) and distributed denial of service (DDoS). By 2023, no fewer than 52 % of API errors processed by Cloudflare were 429 codes (too many requests).
- Injection Flaws
Attackers can insert malicious code (such as SQL injectionsNoSQL, or command) in API requests to gain unauthorised access to databases or underlying systems, or to manipulate data.
- Mass Assignment
APIs that do not correctly validate input data can enable an attacker to modify several parameters in a single API request, potentially to gain unauthorised access or alter critical information.
- Security Misconfiguration
Poor management of exposed APIs, in particular the failure to remove old, obsolete or test versions, opens up security gaps that can be exploited by sophisticated attackers.
- Improper Asset Management
Poor management of exposed APIs, in particular the failure to remove old, obsolete or test versions, opens up security gaps that can be exploited by sophisticated attackers.
- Inadequate Logging and Monitoring
A lack of adequate monitoring and detailed logging of API activity makes it extremely difficult to detect and respond to security incidents quickly and effectively, allowing attackers to remain undetected for longer.
- Server-Side Request Forgery (SSRF)
This vulnerability allows the API to be manipulated to target other internal or external systems using carefully crafted requests, thereby bypassing security controls.
- Third-party attacks
A trusted partner whose legitimate API key has been compromised can be used as an entry point to access the target API in an unauthorised manner.
Best practices for securing APIs
To establish a truly robust API security strategy, it is imperative to adopt a methodical approach and multilayer. This approach must incorporate rigorous technical measures and robust organisational processes throughout the entire API lifecycle, from design to decommissioning.
1. Robust authentication and authorisation
The first and most fundamental line of defence is theauthentication. It is absolutely essential to use strong authentication mechanisms and to standardise them across all your APIs.
- API keys These are simple to implement, but have significant limitations. They generally do not include time information and can be compromised if intercepted. Avoid relying solely on API keys; if they are used, combine them with other mechanisms and do not expose them in URLs, logs or error messages. A French start-up exposed its API keys on GitHub, giving access to sensitive customer data.
- Tokens JWT (JSON Web Tokens) JWT tokens are gaining in popularity because they include information about the user and their permissions, along with an expiry date. BlaBlaCar, for example, makes extensive use of JWT tokens to secure its mobile APIs, forcing regular re-authentication. JWTs should be used internally; for external customers, opaque tokens are preferable.
- OAuth 2.0 OAuth: this protocol is the benchmark for managing authorisation delegation, enabling an application to act on behalf of a user on another service without ever revealing the user's identifying information (such as their password). Platforms such as Okta offer centralised management of API access policies via OAuth 2.0, simplifying the implementation and management of complex authorisations.
- MFA (Multi-Factor Authentication) MFA: impose MFA for logins, payments and password resets to add an extra layer of security against automated attacks.
- Fine, granular access control (Scopes & Claims): use OAuth "scopes" for global access control (for example, to determine whether a user is authorised to query a resource). In addition, implement granular access control at API level by using token 'claims' to check whether the caller has specific rights to particular data or actions. As mentioned, the OWASP Top 10 API Security lists BOLA as the main vulnerability, and granular access control is the best defence.
- Key rotation Just as locks are changed regularly to reinforce physical security, API keys need to be renewed periodically, ideally via an automated process. At Criteo, the automatic rotation of API keys every 90 days has reduced incidents of compromised keys by 80%.
- Architecture Zero Trust The Zero Trust principle is fundamental: don't implicitly trust any entity, whether internal or external. Every API request must be systematically authenticated, authorised and continuously verified, even if it comes from inside your network.
2. Encryption and protection of data in transit
- HTTPS (TLS/SSL) HTTPS is the absolute minimum standard for protecting the confidentiality and integrity of data in transit. All API communications, including those internal to your infrastructure, should imperatively use HTTPS to prevent eavesdropping and tampering. Use the latest versions of TLS.
- Encryption application For particularly sensitive data, additional encryption is required at application level. Société Générale uses double encryption for its banking APIs, even though the HTTPS channel is already decrypted.
- Certificate management Automating the renewal of TLS certificates is essential to avoid service interruptions due to expiry. OVHcloud manages over 100,000 TLS certificates for its customers using an automatic renewal system, reducing 99 % incidents.
3. Validation and sanitation of entries
- Principle of mistrust by default Any data sent to an API must be considered as potentially dangerous until proven otherwise.
- Format validation Check that the data received corresponds to the expected format (for example, a numeric field must be a number, an email address must have a valid structure). Any data that does not comply must be rejected.
- Sanitation (cleaning) Data filtering: meticulously clean incoming data to neutralise any potentially dangerous elements, even if they appear valid at first glance. This includes filtering out special characters and HTML/JavaScript tags.
- Prevention of attacks by injection use prepared queries (for databases) and rigorously validate all entries to effectively counter SQL injections, XSS (Cross-Site Scripting) and other types of injections.
4. Rate limiting and DDoS protection
- Rate Limiting imposes strict limits on the number of requests an individual client can make in a given period of time. Leboncoin, for example, applies different levels of limitation: 100 requests/hour for anonymous users, 1000/hour for authenticated users, and 10,000/hour for professional partners, thus adapting the policy to needs.
- DDoS protection requires more sophisticated measures to absorb or block massive volumes of malicious requests that attempt to overwhelm the API and render it unavailable. OVHcloud has demonstrated its resilience resisting a DDoS attack of 840 Gbps in 2023 thanks to a distributed architecture and automatic filtering systems. Cloudflare, a leader in this field, blocks an average of 182 billion malicious requests a day.
- Use of WAF (Web Application Firewall) A WAF is deployed upstream of the API to analyse and block requests and responses that infringe predefined security rules or target known vulnerabilities, acting as a protective shield.
5. Monitoring, logging and intrusion detection
- Comprehensive logging logs: capture all the essential information about each API request (who made the request, when, the response received, the duration of the request). These logs are crucial for quickly detecting suspicious activity. However, it is vital to avoid logging sensitive or confidential information.
- Behavioural analysis The API: establish baselines of normal behaviour for your APIs and your users so that you can identify anomalies and significant deviations. Artificial intelligence can greatly assist in detecting complex patterns that would otherwise escape traditional monitoring.
- Real-time alerts Alert systems: set up alert systems to immediately notify the appropriate security personnel when potential incidents are detected, including for so-called "low and slow" attacks which are designed to be stealthy.
6. API lifecycle management and governance
- API Gateways These gateways centralise traffic management and apply specific security policies to all requests. This means you can implement and manage critical security features such as rate limiting, request blocking, logging, authentication and authorisation for all incoming API requests. Imperva Cloud WAF, Cloudflare API Gateway and WAF Gateway are examples of complete solutions.
- Inventory and discovery of API Maintain an up-to-date and complete inventory of all exposed APIs, including Shadow APIs. Specialist tools such as AppTrana, Cloudflare API Gateway, Graylog API Security and Cequence offer automatic API discovery capabilities to help you with this task.
- Ongoing audits and penetration tests Integrate security testing throughout the development cycle (security approach). DevSecOps). Automated tests, fuzzing, vulnerability scans and manual audits (penetration tests) are essential to identify vulnerabilities before they are exploited. Solutions such as Probely and APIsec can be integrated into CI/CD pipelines to automate security testing.
- Separation of departments Segmentation: logically and physically separate internal API services from those directed towards the outside world. This segmentation prevents external attacks from propagating and directly affecting critical internal business processes.
- Adaptive strategy Don't implement all mitigation techniques simultaneously and statically. Adopt an adaptive approach by dynamically adjusting rate limits, access controls and bot detection mechanisms based on real-time traffic patterns and observed risk levels.
Defence in depth: operational security
Once deployed, an API requires continuous protection. A layered defence strategy, combining complementary tools, is the most effective way of blocking threats in real time.
Protective layers
Filters out known attacks (SQLi, XSS) and malicious requests based on signatures.
Manages authentication, authorisation, rate limiting and routing.
Your API services
The role of AI in securing APIs
Artificial intelligence is a double-edged sword when it comes to API security. On the one hand, it is exploited by attackers to fuel increasingly sophisticated bot attacks that are difficult to detect. The polymorphic botsFor example, they can constantly change their appearance and behaviour to evade traditional defences.
On the other hand, AI is a valuable and powerful ally for defence. AI-powered surveillance systems are able to process massive volumes of API traffic in real time and detect threats with far greater accuracy than manual or fixed rules-based methods.
AI can significantly refine bot detection by continuously adapting to new threats, providing advanced behavioural analysis that effectively differentiates legitimate human interactions from malicious bot activity.
To find out more, read our white paper :
What tools are needed to secure APIs?
The market offers a multitude of tools for strengthening API security:
- Complete API security platforms Application security: solutions such as Imperva Application Security, Cloudflare API Shield, AppTrana, Cequence and 42Crunch offer suites of integrated features. They often offer automatic API discovery, comprehensive protection against the top 10 OWASP API vulnerabilities, advanced protection against bots and DDoS attacks, and data leak detection.
- Testing and monitoring tools Tools such as Postman, Apache JMeter, Assertible, Insomnia, Karate, Katalon Studio, Sauce Labs Platform for Test, SoapUI/ReadyAPI and Swagger are essential for designing, developing, testing and monitoring not only the performance but also the security of APIs throughout their lifecycle.
- Authentication and authorisation solutions The OAuth solution: suppliers such as Okta and Curity specialise in centralised management of authentication and authorisation, particularly for OAuth servers, guaranteeing secure management of identities and access to APIs.
Securing APIs: a strategic imperative
Securing APIs is not just a technical option, it's a strategic imperative for the long-term future of your organisation.
Faced with the exponential increase in the number of APIs deployed and the growing sophistication of bot attacks, a proactive, multi-layered and continually adaptive approach is essential.
By investing in good security practices, adopting the right tools and actively promoting an integrated security culture from the earliest stages of development (DevSecOps)You are building the foundations of a sustainable, resilient and trustworthy digital ecosystem.
In doing so, you turn the challenge of API security from a simple constraint into a genuine competitive advantage, protecting your most valuable assets and ensuring the confidence of your users and partners.




