With unprecedented computing power, the quantum computer could break the algorithms of encryption the safety of our customers. sensitive data on a global scale. Cryptography experts are already preparing their response.
In the not-too-distant future, ten years or more, "Q Day" will occur, marking what is known as "Q Day". quantum supremacy ". On that day, a quantum computer will outperform the most powerful supercomputers in certain calculations.
Quantum computing uses "qubits" or quantum bits. Unlike conventional bits, which can only take two values (0 or 1), qubits can be in quantum superposition. This means that they can be both 0 and 1 simultaneously.with specific probabilities. What's more, qubits can be interconnected, multiplying their possible states and computing power.
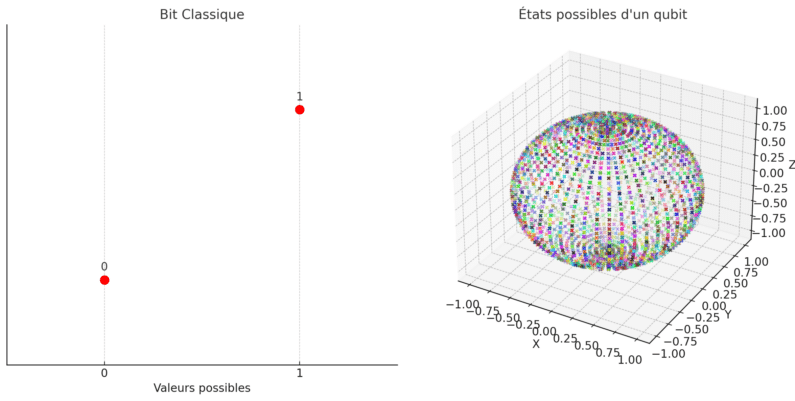
The power of quantum computers is measured in qubits. A 53-qubit computer can process 53 qubits simultaneously. This corresponds to a superposition of 9,007,199,254,740,992 possible states (2^53). In other words, instead of manipulating just 5 binary states like a traditional computer, the quantum machine processes 9 million billion bit configurations in parallel!
This characteristic gives quantum computing such computing power that it will consign current supercomputers to oblivion.
In 2019, Google demonstrated that its 53-qubit Sycamore quantum computer could perform a complex calculation in 3 minutes that would take around 10,000 years to complete than a conventional supercomputer!
In June 2024, Quantinuum, Honeywell's quantum computing company, set a new record. Its 56-qubit H2-1 computer outperformed Sycamore by 100 times. All the while consuming 30,000 times less energy than a conventional supercomputer!
The current challenges of quantum computing
Technology giants such as IBM, Google and China's Baidu are currently developing prototypes of quantum computers. These machines, while impressive, face major technical challenges.
In particular, they need to improve their stability and reduce their error rate. Quantum computers also need to be protected against external magnetic interference. They also need to be cooled to a temperature close to absolute zero (-273.15°C), making this technology difficult to access for the time being.

The world of cryptography under threat
While we wait for the first mass-market quantum computers, due in 2035 at the earliest, the question of how they will be used is already being raised. This power could improve weather forecasts or simulate the effects of a molecule for new medicines or materials.
But what would happen if this technology fell into the wrong hands, a rogue state or a criminal group? Visit cyber securityThe power of quantum computers would challenge the very foundations of current cryptography.
Encryption algorithms (AES, RSA) and public key infrastructures (PKI) currently secure our browsing, communications and transactions on the Internet. With quantum computing, they could be broken or become vulnerable.
Two encryption methods dominate: RSA, based on factoring large numbers, and ECC (Elliptic Curve Cryptography), which uses elliptic curves to improve efficiency and security.
The security of today's cryptographic systems is based on the difficulty that conventional computers have in factoring large numbers and solving discrete logarithms.. Factoring a 1024-bit RSA key, which is still frequently used, involves breaking down a number of around 309 digits from the public key into two prime factors of 512 bits each.
However, quantum computers, usingShor algorithmcan perform these calculations exponentially faster, making current cryptosystems vulnerable.
“ Any cryptographic system is, by definition, breakable.
Philippe Nieuwbourg, independent analyst and trainer at ORSYS a course dedicated to quantum computing
It's only a question of time and therefore of computing power. Today's keys are sufficiently complex and robust to discourage malicious organisations. Similarly, a burglar will not attack an armoured door if it takes several hours to open it.
Cybercriminals are already taking action
This threat is all the more worrying given that malicious actors are already taking action. They apply the principle of harvest now, decrypt later "(collect now, decipher later).
According to this strategy, large volumes of sensitive data have already been intercepted and stored. This data includes plans for nuclear power plants, encrypted diplomatic communications secrets The attackers hope to decipher them once quantum computers are available.
91 % attacks by ransomware include an attempt to exfiltrate data
The State of Cybersecurity: 2024 Trends" report by Arctic Wolf, 2024
The cybercriminals has changed. Ransomware attacks have moved from a two-stage model (infiltration and encryption) to a three-stage model: infiltration, data exfiltration and then encryption.
The attackers' main objective has shifted from rapid financial extortion to obtaining sensitive information to sell or exploit at a later date..
Preparing now to post-quantum
“ The quantum threat is no phantom menace, and we need to start preparing for it now. "says Samir Battin, CISO at Signaturit Group, European leader in digital identity and electronic signature solutions. In the age-old race between the policeman and the thief, the response is already being organised in the world of cryptography.
Faced with this threat, the scientific community and standards bodies are working actively to develop cryptographic solutions that are resistant to quantum attacks.
Using PQC and post-quantum algorithms
In an opinionthe Agence nationale de la sécurité des systèmes d'information (ANSSI) recommends the use of post-quantum cryptography (PQC). This cryptography encompasses algorithms that are resistant to attacks from both classical and quantum computers.
Advantage: these post-quantum algorithms can be run on conventional computers.
In August 2024, the National Institute of Standards and Technology (NIST), the US federal agency responsible for setting standards and promoting innovation, published the final versions of its first three post-quantum cryptography (PQC) standards:
- L-KEM (derived from CRYSTALS-Kyber) a key encapsulation mechanism for general encryption
- ML-DSA (derived from CRYSTALS-Dilithium) a general-purpose digital signature algorithm based on networks
- SLH-DSA (derived from SPHINCS+) a stateless digital signature scheme based on hashing.
NIST selected these algorithms for their resistance to quantum and classical attacks. They are also compatible with existing systems. NIST is encouraging organisations to adopt these new standards now. It stresses the importance of preparing security systems for the quantum era.
In France, the ANSSI has drawn up its own list, without making any recommendations.
Quantum ready" encryption solutions coming soon
ANSSI recommends the principle of hybridisation. It encourages cryptologists to combine PQCs with conventional algorithms. "By combining the best of both worlds, this approach makes it possible to raise the level of security and protect against potential risks. vulnerabilities post-quantum algorithms in the face of the computing power of traditional computing", says Samir Battin. Currently in the research phase, Signaturit has set itself the target of generating quantum signatures by 2030.
The publisher is not the only one in the starting blocks. Funded by the France 2030 programme and the European Union, the Hyperform consortium, coordinated by smart card component manufacturer Idemia, brings together eight French players who are leaders in the fields of cybersecurity and post-quantum technology, including encryption specialist Prim'X. The aim is to develop a sovereign solution that is resistant to quantum computers.
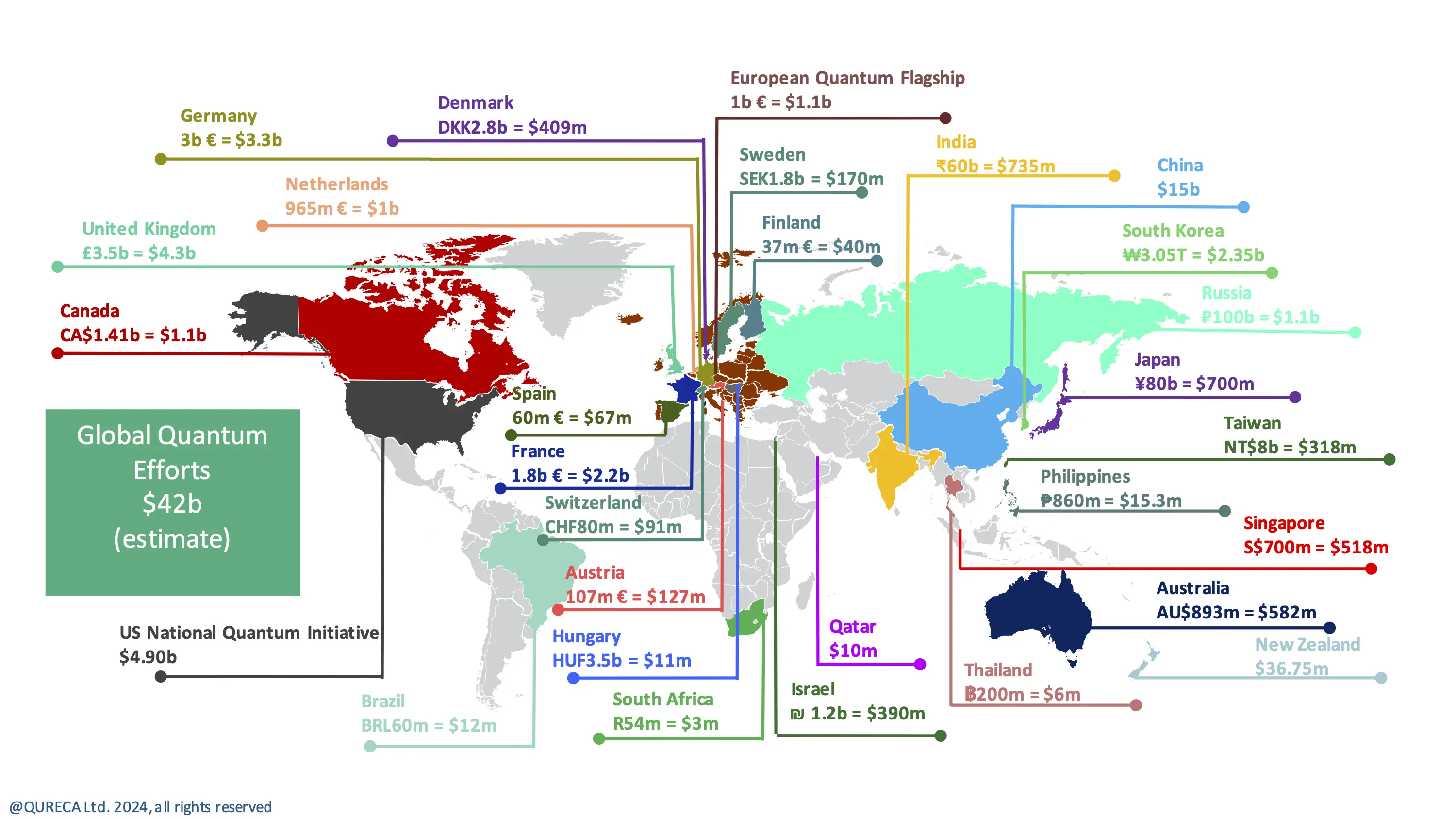
By June 2024, global investment in quantum computing will exceed $40 billion, according to quantum technology consultancy QURECA.
Assessing risks, mapping sensitive systems
While suppliers of encryption technologies are organising their response, businesses should not sit idly by. The defence, aerospace, finance, telecoms and healthcare sectors are particularly at risk. " The worst mistake would be to bury our heads in the sand "warns Philippe Nieuwbourg.
In his view, companies must assess the threat based on the standard ISO 31000 risk management. "What is the risk of this quantum threat occurring in my business? This risk will be weighted by the level of impact envisaged. In the banking sector, the impact would be colossal, given the current protection of financial transactions. ".
Following this assessment, the company draws up an action plan to reduce the probability of occurrence or its impact. For example, a company might decide to change its channels for transmitting sensitive information. Alternatively, it needs to map all the systems using cryptography to prepare them for the post-quantum world.
The transition to a post-quantum world represents a major technical and organisational challenge. Although the threat is not immediate, it is crucial to anticipate this development. Businesses and governments must act now to guarantee the long-term security of their data.
💡 IN BRIEF
How can we prepare for the quantum threat?
- Risk assessment Identify critical assets and processes that depend on current cryptography.
- Cryptographic inventory Map all systems using potentially vulnerable algorithms.
- Technology watch Keeping abreast of advances in post-quantum cryptography.
- Progressive update adopting a hybrid approach combining classical and post-quantum algorithms.
- Training Raising teams' awareness of the challenges of post-quantum security.





